Ethical Hacking: Enumeration Practice (Journal 1)
by jerdy on 27/03/2019We were given an assignment and was asked to fulfil the following:
- Network and IP Space pentest.id
- Enumeration User hackme.pentest.id
- Enumeration User Email @pentest.id
We were recommended to use the following tools:
- wpscan
- jooscan
- TheHarvester
- Nmap
The following is my solution:
Network and IP Space pentest.id
I used theharvester to check any hostnames IPs available.
I typed the following in terminal:
![]()
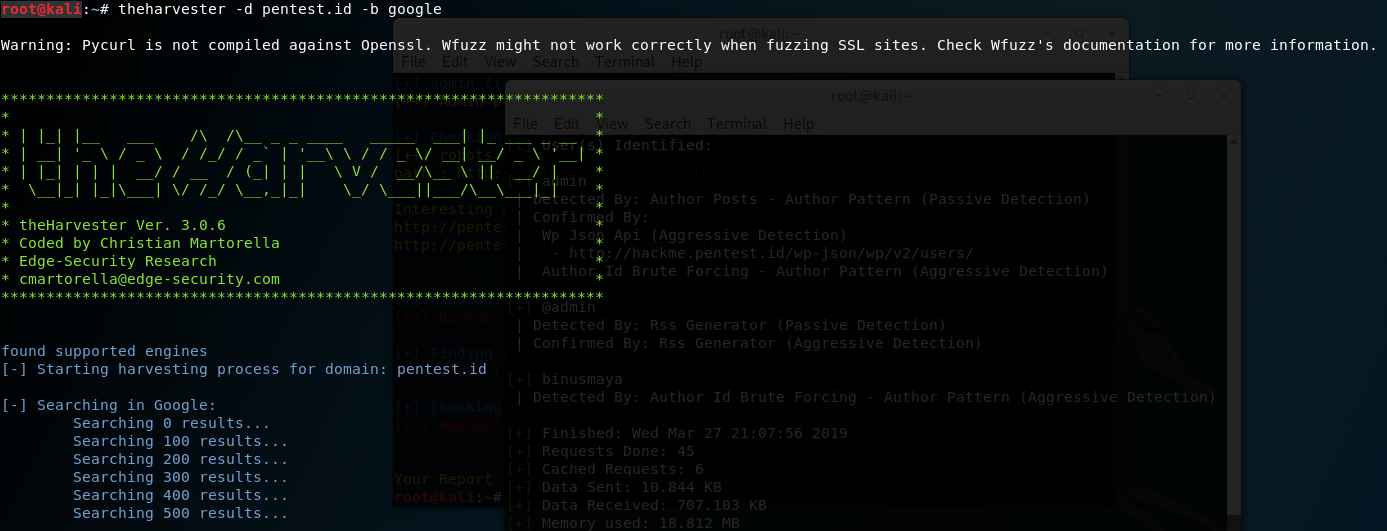 No need to worry about the “warning” because it is just telling us that theHarvester does not work in any site that has ssl.
No need to worry about the “warning” because it is just telling us that theHarvester does not work in any site that has ssl.
The function of -d is to search for any domain or name of a company.
The function of -b is to choose the data source such as bing, google, twitter, etc.
After typing “theharvester -d pentest.id -b google”, I received the results as the following:

Enumeration User hackme.pentest.id
I used wpscan to enumerate user from hackme.pentest.id and typed the following:
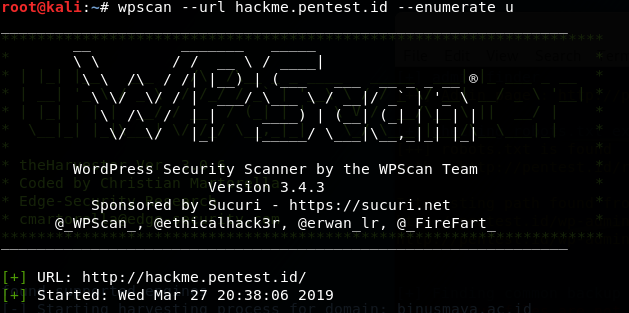
” –url ” is used to scan the url of the blog we want to scan.
” –enumerate u ” means enumerating users.
It produced the result as the following:
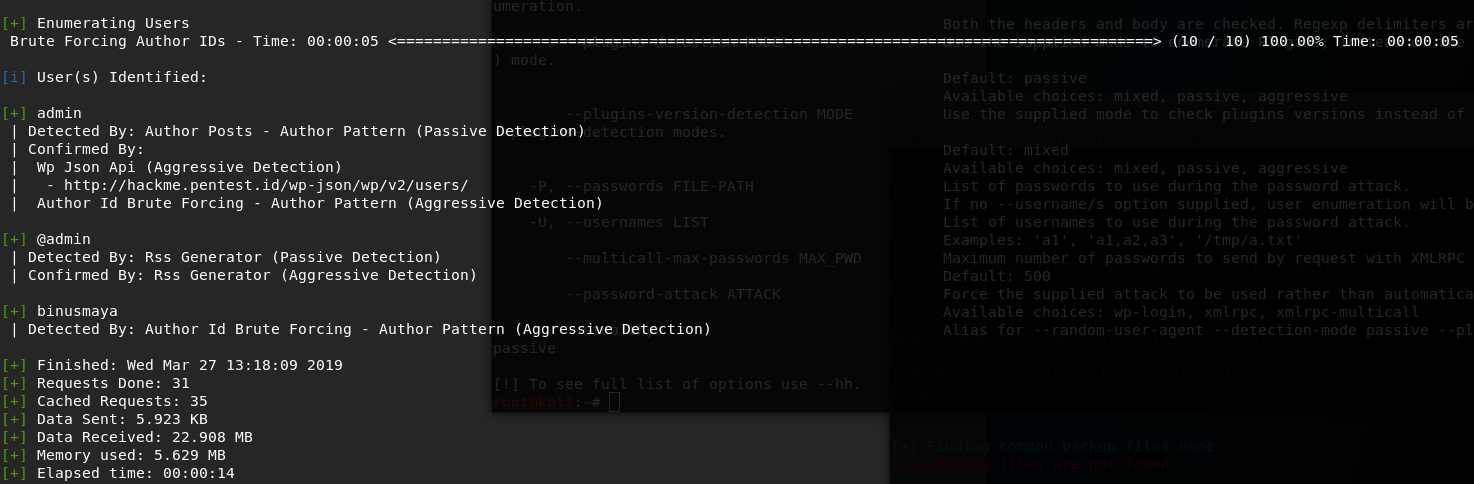
Enumeration User Email @pentest.id
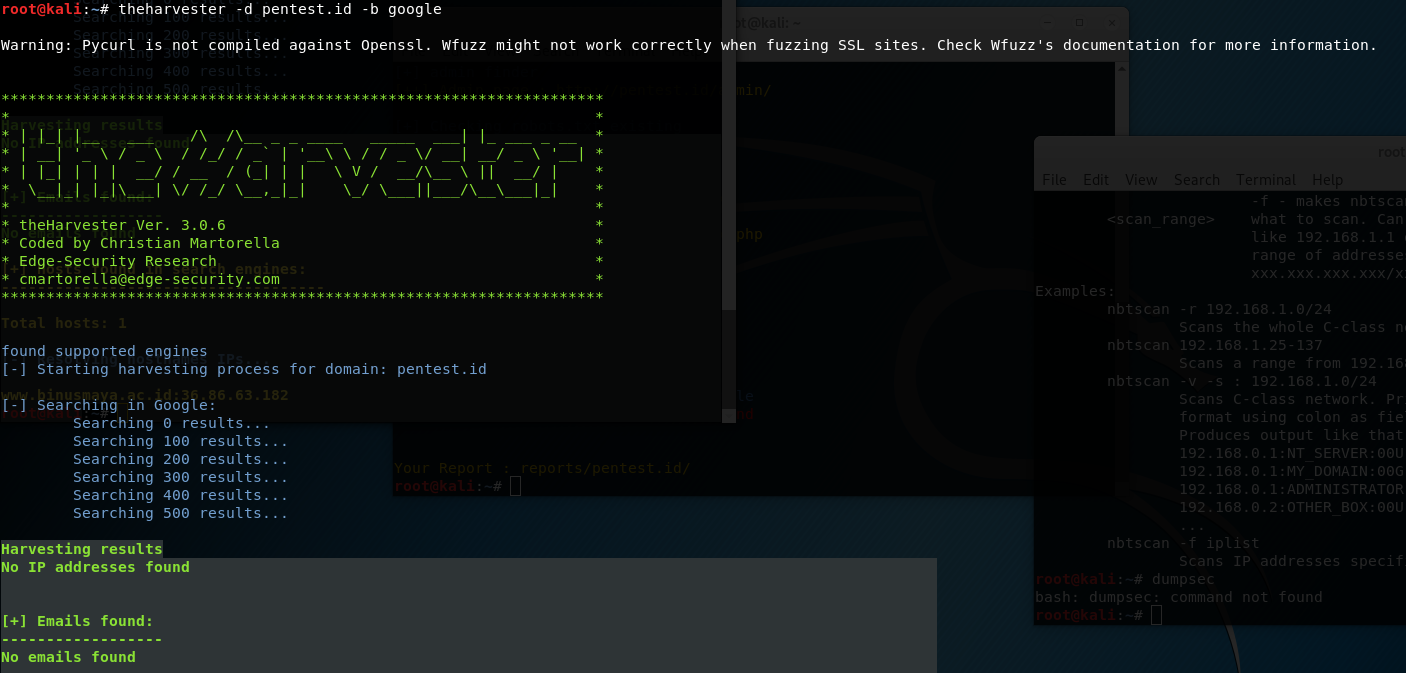
I used theharvester and typed “theharvester -d pentest.id -b gooogle”, but unfortunately there was no email found.
There are 262 comments in this article: