29/03/2019
Kali Linux provides many tools for information gathering.
For this post, I am going to introduce Nmap:
What is Nmap?
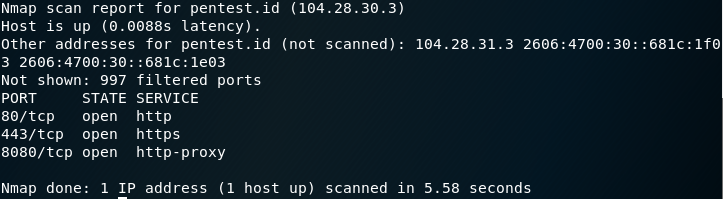
Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and network discovery. Network administrators use Nmap to identify what devices are running on their systems, discovering hosts that are available and the services they offer, finding open ports and detecting security risks.
How to use Nmap?
nmap *domainname*
Example: nmap pentest.id

29/03/2019
Kali Linux provides many tools for information gathering.
For this post, I am going to introduce whois:
What is Whois? When to use it?
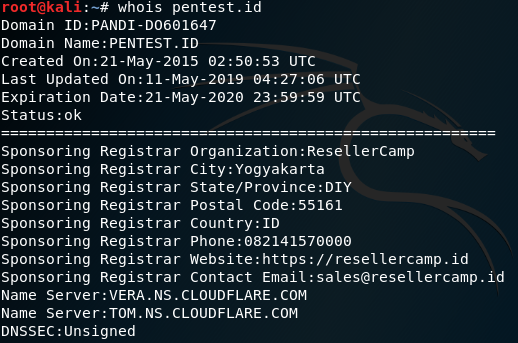
Whois is a widely used Internet record listing that identifies who owns a domain and how to get in contact with them.
The Internet Corporation for Assigned Names and Numbers (ICANN) regulates domain name registration and ownership. Whois records have proven to be extremely useful and have developed into an essential resource for maintaining the integrity of the domain name registration and website ownership process.
How to use Whois?
28/03/2019
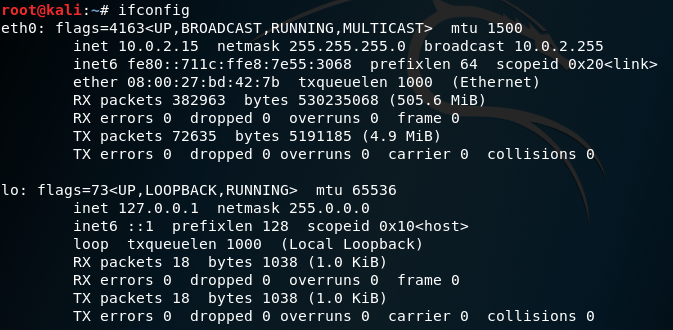
To discover our IP, type ifconfig
27/03/2019
We were given an assignment and was asked to fulfil the following:
- Network and IP Space pentest.id
- Enumeration User hackme.pentest.id
- Enumeration User Email @pentest.id
We were recommended to use the following tools:
- wpscan
- jooscan
- TheHarvester
- Google
- Nmap
The following is my solution:
Network and IP Space pentest.id
I used theharvester to check any hostnames IPs available.
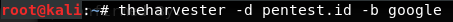
I typed the following in terminal:
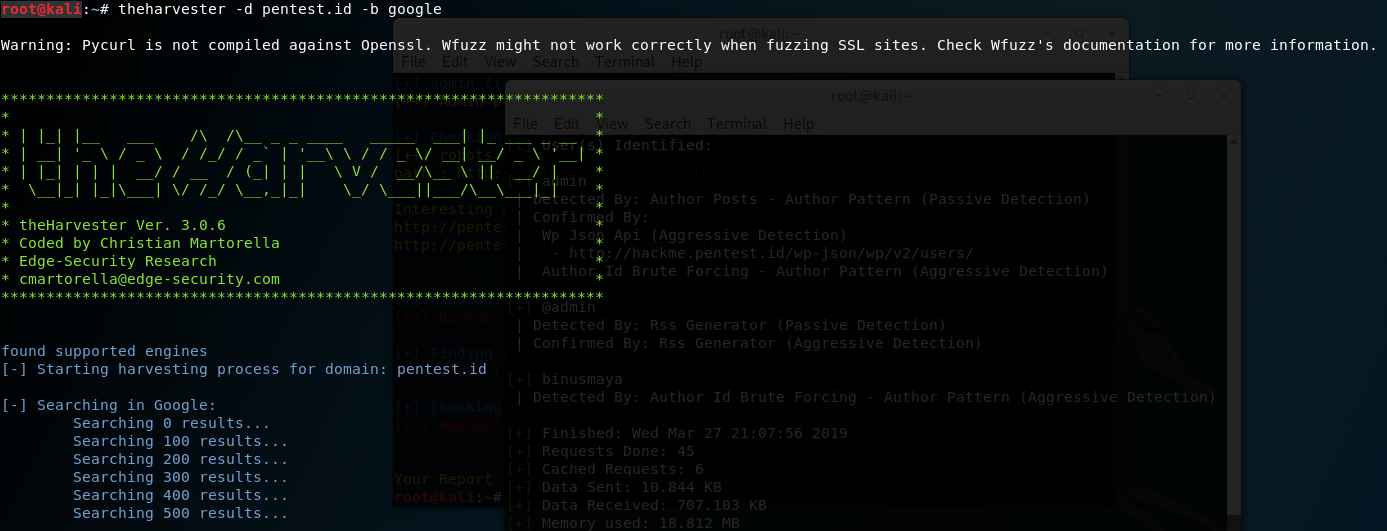 No need to worry about the “warning” because it is just telling us that theHarvester does not work in any site that has ssl.
No need to worry about the “warning” because it is just telling us that theHarvester does not work in any site that has ssl.
The function of -d is to search for any domain or name of a company.
The function of -b is to choose the data source such as bing, google, twitter, etc.
After typing “theharvester -d pentest.id -b google”, I received the results as the following:

Enumeration User hackme.pentest.id
I used wpscan to enumerate user from hackme.pentest.id and typed the following:
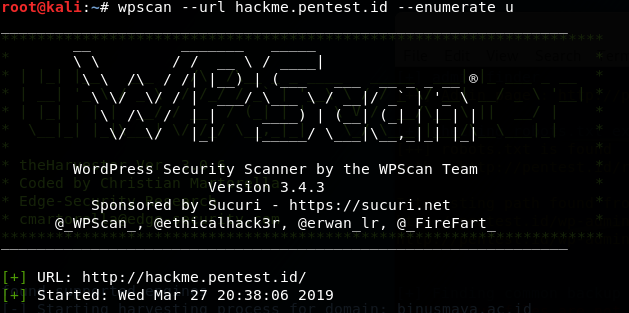
” –url ” is used to scan the url of the blog we want to scan.
” –enumerate u ” means enumerating users.
It produced the result as the following:
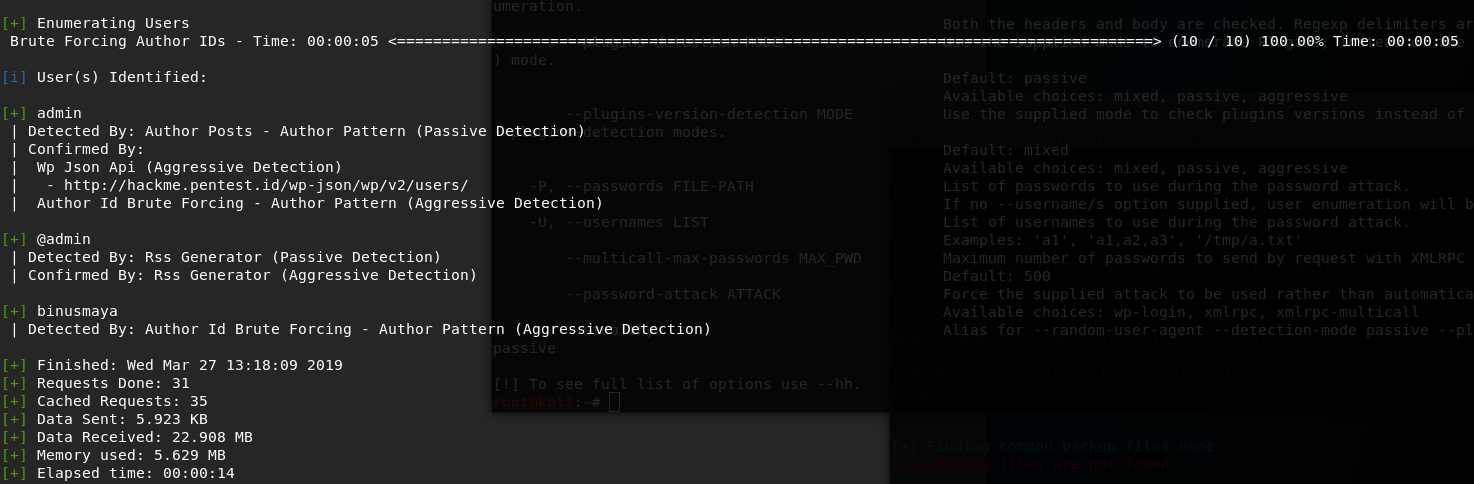
Enumeration User Email @pentest.id
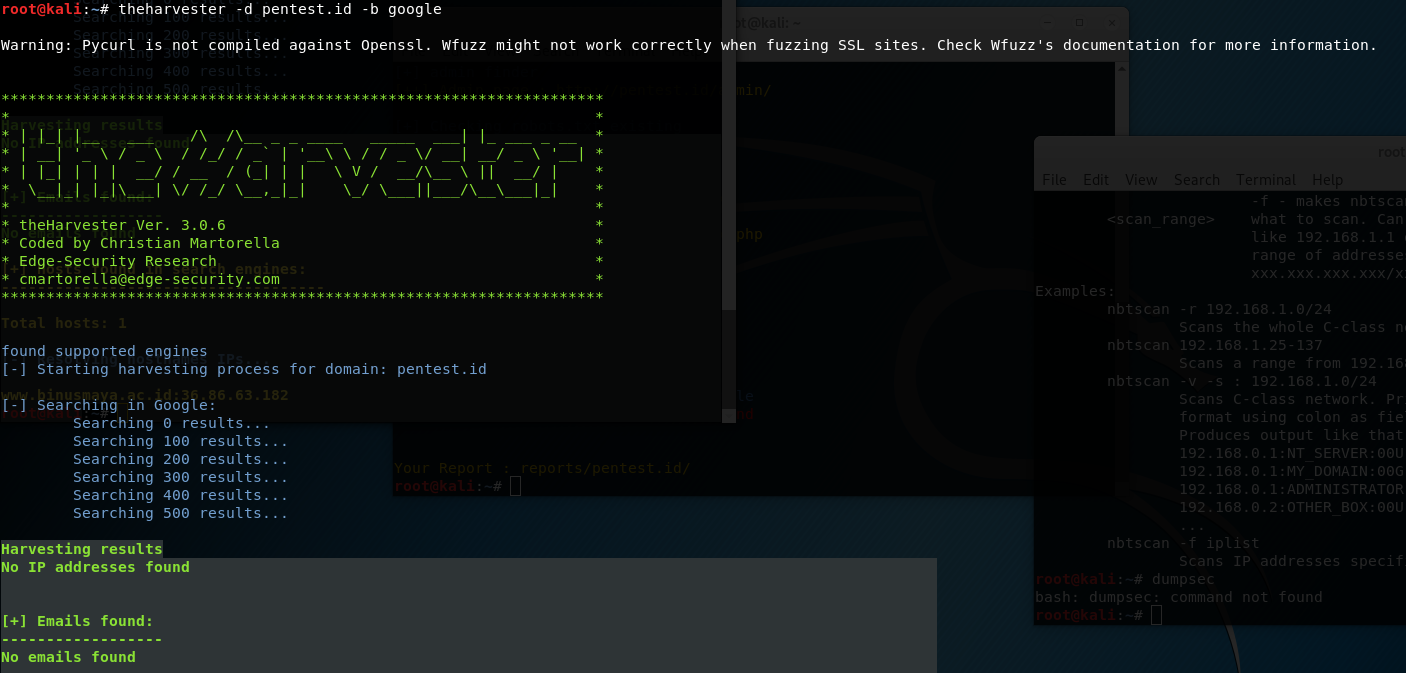
I used theharvester and typed “theharvester -d pentest.id -b gooogle”, but unfortunately there was no email found.
![]()







