Ethical Hacking: Nikto
1/06/2019What is Nikto?
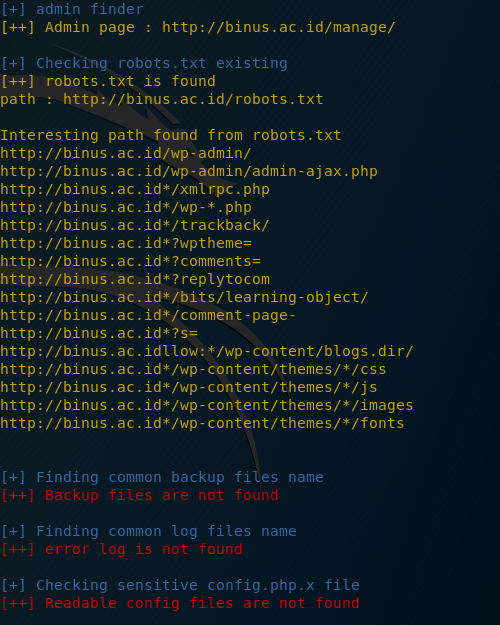
Nikto is a simple, open-source web server scanner that examines a website and reports back vulnerabilities that it found which could be used to exploit or hack the site. Also, it’s one of the most widely used website vulnerabilities tools in the industry, and in many circles, considered the industry standard.
Although this tool is extremely effective, it’s not stealthy at all. Any site with an intrusion-detection system or other security measures in place will detect that it’s being scanned. Initially designed for security testing, stealth was never a concern.
How to use Nikto?
Basic syntax: nikto -h <IP or hostname>
Nikto is capable of doing a scan that can go after SSL and port 443, the port that HTTPS websites use.
Scanning an SSL-enabled Site
syntax: nikto -h <IP or hostname> -ssl
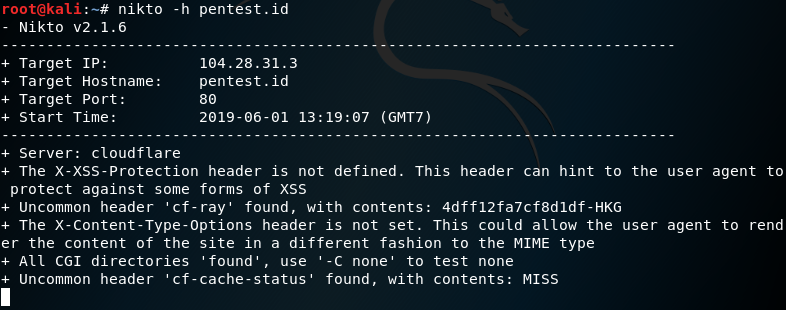
let’s start with scanning binusmaya.binus.ac.id.
After it connects to port 443, we see that there’s some useful information about the cipher and a list of other details like that the server is Nginx.
Scan a HTTP Website

Scan an IP Address
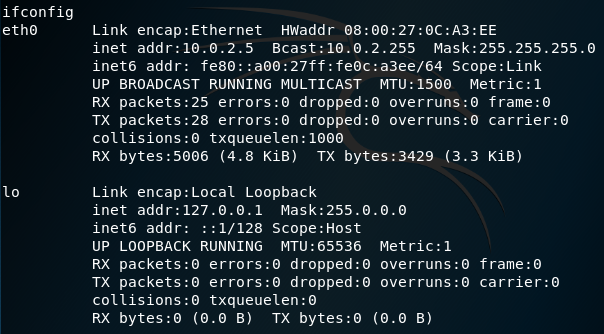
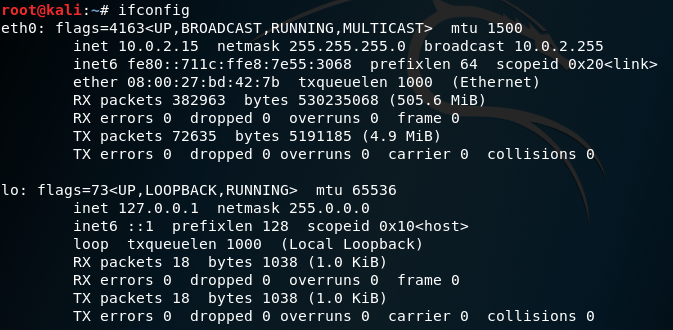
Let us find our IP address using ifconfig.
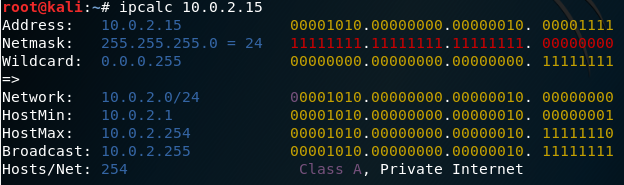
Then we can run ipcalc to get our network range.
To install ipcalc, type apt install ipcalc
We run Nmap to find services running in the network range.
Let’s scan port 80 with our range and tack on -oG (grepable output) to extract only the hosts that are up and running
Then we’ll save everything to a file, which I’m naming nulbyte.txt, but could be named anything.

We use cat to read the output stored in our nulbyte.txt document (or whatever you named it).
- awk, a Linux tool that will help search for the following pattern
- Up means the host is up
- print $2 means to print out the second word in that line for each

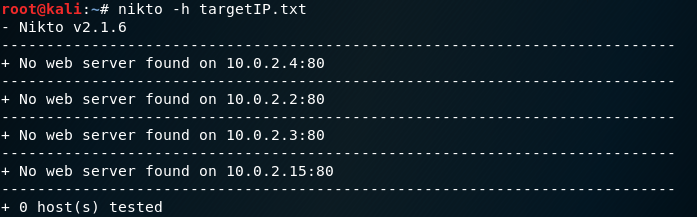
We can now view the contents of our new file with cat to see all the IP addresses that have port 80 open.
References
https://null-byte.wonderhowto.com/how-to/scan-for-vulnerabilities-any-website-using-nikto-0151729/